What is Cloud Security?
Cloud security encompasses in itself a mechanism, a collection of measures that helps an organization mitigate both internal and external threats. Cloud security becomes a major factor in an organization’s list of priorities as they move forward with their digital transformation strategy. Cloud-based tools and services can help an organization strengthen their information security.
Most common problems faced by organizations without cloud security
- Safeguard Data Security: In the absence of cloud security, your organization would need more control tools, misconfiguration, and identity access management.
- Multi-Cloud Environment: It is challenging to track security challenges and requirements in a multi-cloud environment without cloud security.
- Risk of Data Loss: Recovering your data becomes a risky path to take when you have no backup to work with.
- No Disaster Recovery Plan: Any business requires to recover quickly from an unforeseen attack, to resume day-to-day operations. In the absence of a disaster recovery plan your business is bound to face issues like data loss, reduced productivity.
According to Statista’ findings, 66% are apprehensive about data privacy and confidentiality in the cloud environment.
Most common problems faced by organizations while taking up cloud security
- Compliance Issues: Maintaining strict compliance in a hybrid or multi-cloud environment is challenging and can lead to a lack of visibility.
- Data Loss: A significant concern is data loss, stemming from various factors. Security misconfigurations in cloud storage can expose data to risks.
- Downtime: Operations can be disrupted by downtime issues with service outages, technical issues, cyberattacks, etc.
- Identity Access & Management: Without proper user control measures, your infrastructure is under a constant threat. It can fall prey to data breaches, identity theft, etc.
Most common problems faced by organizations after migrating to cloud with security
- Configuration Errors: Errors in settings can lead to vulnerabilities, making systems susceptible to breaches.
- Denial-of-Service Attacks: Overwhelming traffic disrupts services, causing downtime and potential data exposure.
- Data Loss with Cyberattacks: Intrusions or ransomware incidents may result in critical data loss.
- Insecure Control Points: Weak access controls invite unauthorized entry, compromising data integrity.
- Unreliable Threat Notifications: Delayed or incomplete alerts hinder swift responses to emerging security threats.
Costs associated with cloud
Managing a resilient IT infrastructure involves overseeing critical elements that collectively impact the budget. This includes infrastructure costs, which encompass expenses related to hardware, networking devices, and data storage solutions. Licensing expenses are also significant, covering software licenses and ongoing subscriptions. Additionally, resource allocations, such as IT staff salaries, training programs, and fees for outsourcing specialized tasks, make up a substantial portion of the financial plan. These interconnected costs can strain your budget. To strike a harmonious balance among these expenditures, Rapyder can be your partner in efficiently managing a cost-effective and high-performance IT infrastructure.
Who can be your reliable/proven cloud security partner?
- Service providers who have a reputation in the industry and years of experience in the field to gauge their reliability.
- Service providers who have the qualifications, skills, and competency to ensure they can meet your security needs.
- A security partner who provide a range of services that match your specific requirements.
- Partners who offer powerful reporting tools for ongoing performance evaluation.
- Service providers whose solution adapts and scale according to your business requirements.
What to include your cloud security journey?
Listed below are a few areas that demand focus for your cloud security journey-
- Threat Modelling: Identify and address threats in systems, such as cloud architectures, applications, IoT devices, and business processes, by defining countermeasures for prevention and mitigation.
- Fix Misconfigurations: Address cloud vulnerabilities, especially security misconfigurations, which often involve overly permissive firewall rules or security groups.
- Contain Network Access: Create and maintain network diagrams to understand and assess your cloud environment’s dynamic nature, helping teams ensure security.
- Improve Resource Access: Establish secure and private connectivity to cloud resources, potentially through VPN setups or bastion/jump boxes.
- Securing IAM Policies: Strengthen security by maintaining robust Identity and Access Management (IAM) policies, reducing potential damage in case of a breach.
- Implementing Logging and Monitoring: Essential for identifying issues and uncovering malicious events, security logging and monitoring are crucial components of a cloud security program.
Time frame of implementation
The timeframe for executing services fluctuates based on the intricacy and scale of the project. Generally, it encompasses several crucial stages, such as initial planning, development, testing, deployment, and continuous maintenance.
Below are the details of the estimated timeframe for a few services:
| Service | Timeframe* |
| POC | 1 Week |
| SOW | 2 Days |
| NDA | 2 Days |
| Initial Reviews | 1 Day |
| Planning Phase | 1 Day |
| Service Addition | 3-6 Weeks |
| Testing and handover managed services | 2 Days |
Best practices while taking up cloud security
- Develop a comprehensive cloud security strategy to protect your infrastructure and data.
- Select a trusted cloud service provider that aligns with your security requirements.
- Maintain lucidity with your cloud security partner to distribute jobs and harden security areas.
- Implement network segmentation to enhance security and isolate sensitive components.
- Provide adequate user training to all your users, as they are your primary protection system.
- Execute a stringent password security policy to protect against unauthorized access.
- Strengthen the cloud endpoints to prevent vulnerabilities.
- Utilize strong encryption to safeguard data in transit and at rest, as your data can fall into a higher risk.
- Develop and enforce disaster recovery procedures to ensure business continuity.
- Adhere to necessary compliance standards and regulations to maintain legal and security requirements.
Start and Sustenance
- Security Strategy: When it comes to securing your cloud infrastructure, whether setting up a new environment or migrating your existing infrastructure, the approach can vary based on your architecture. We’re here to assist you in both scenarios. Additionally, you can improve your infrastructure and reduce expenses by considering our Architecture Assessment and License Optimization services.
- Ongoing Infrastructure Care: Our cloud management services have earned top ratings from both our OEM partners and customers across various industries. Our dedicated 24/7 customer support team is well-prepared to handle unexpected situations with minimal disruption for our clients. We provide timely notifications regarding security risks, cost analysis, system patterns, optimization suggestions, and more to ensure a smooth experience in the cloud environment.
How Rapyder helps with its full-stack cloud services?
Rapyder brings you the latest cloud security to strengthen the current security of your enterprise. Due to security and data protection concerns, enterprises often need help sharing their data on cloud platforms. This reluctance to embrace cloud services can result in decreased business efficiency, as potential problems that could be easily avoided are allowed to impede progress.
With over a decade of expertise in Information Security Life Cycle Management, we are your reliable partner for security operations. Our comprehensive cloud solutions encompass consulting, implementation, and managed services.
In case of a mishappening, you require a disaster recovery strategy. Here, we offer a comprehensive safety net for your digital assets, storing copies of your data in secure locations, ensuring that even if unexpected events like hardware failures, data corruption, or natural disasters occur, your information remains intact and accessible.
We partner directly with industry leaders such as AWS, Microsoft Azure, and other OEMs. These partnerships help us ensure we can provide you with the most exceptional cloud migration solutions.
Additional benefits from Rapyder
Rapyder offers a range of valuable services to help businesses optimize their cloud journey. We provide Free Cost Assessment services conducted by cloud experts who will analyze your organization’s infrastructure and offer recommendations on cloud type, provider, and resource provisioning to align with budget and business growth.
We specialize in Cloud Consultation and offer Free Cloud Consultation for you. We help businesses reduce IT resources and costs while ensuring high reliability, security, and optimal performance.
Our offers also include a Know Your Architecture program for your business to assess your current cloud setup and outline IT objectives, facilitating a clear migration strategy.
To get started on the public cloud, we offer Free Cloud Credits, especially for start-ups. We help organizations reduce and optimize the cloud service to obtain the most efficient public cloud environment possible.
Our customers can enroll in Rapyder programs for benefits worth above USD 1 million.
These benefits include:
- Mentorship programs from business and technical experts
- Free promotional credits up to $5000
- 25% discounts on regular service fees
- Two months of free support
- Up to 25% off on implementation charges
- Availability of Cloud audit services
- Migration acceleration programs and many more.
Related Case Studies
AWS Cloud Security Case Study of IamHere Software Labs
6 September 2022 About the client: IamHere is a location-first social network providing a hyperlocal…
PayNearBy Built Highly Secure & Reliable Solution to Keep Data Safe
About The Client Incepted in April 2016, Nearby Technologies is a fintech company offering financial/non-financial…
GlobalKart Enhances its Security & Scalability With AWS Infrastructure
12 September 2019 About The Client The idea of GlobalKart was conceptualized in November 2018 with…
AWS Managed Cloud Service Case Study: Travel Firm Achieved Cost Saving
29 August 2019 About The Client Our Customer is a leader in the travel industry…
Testimonials
Types of cloud security

Network Security
Workloads are isolated using a Virtual Private Cloud. To ensure secure access to the application, we provide essential security components such as NACL, Security Groups, Subnets, and VPN access.

Data Security
Data stands as the most crucial asset for any organization. Our expertise lies in safeguarding your data at rest and in motion to ensure compliance with security regulations and meet the highest data protection standards.

Security Information & Event Management
Security Incident and Event Management is rapidly becoming an indispensable component of the security ecosystem. Our solutions excel in aggregating data from various systems and conducting comprehensive analyses to detect abnormal activities and potential cyberattacks.

Identity and Access Management
Rapyder offers comprehensive solutions for user provisioning, access management, and governance reporting, covering hybrid and public cloud environments. We can assist you in efficiently running and managing these critical aspects of your cloud infrastructure.

Security, Governance & Compliance
To facilitate the migration of regulated workloads to the cloud, we provision a compliant VPC infrastructure in the public cloud. This infrastructure adheres to various security standards, including the PCI security standard and the (SOC) 1 standard.

Cloud Access Security
Through our robust firewall and Web Application Firewall (WAF) solutions, we have successfully aided numerous customers in safeguarding their networks and applications against external threats.
Supplementary services we offer
Rapyder provides you with all the modern facilities and services, including:
- Omni-Channel Marketing and Messaging
- Big Data
- Data Analytics and Business Intelligence
- App Modernization
- RPA (Robotic Process Automation)
- Cloud Artificial Intelligence and Machine Learning
- Data Lakes and Warehouses
- Internet of Things
- Database Modernization
- Blockchain and more as the need arises
Industries We Support
We specialize in providing multiple industries with customized cloud solutions, enabling them to a vertical-specific digital transformation.
Industries we have served –
- Aerospace
- Agriculture
- Automotive
- Banking
- Computers & Electronics
- Consumer Goods
- E-Commerce
- EdTech
- Energy & Utilities
- FinTech
- Wholesale & Distribution
- GameTech
- Government
- Healthcare
- Hospitality
- Life Sciences
- GameTech
- Government
- Healthcare
- Hospitality
- Life Sciences
- Travel
- Non-Profit Organization
- None
- Oil & Gas
- Other
- Power & Utilities
- Professional Services
- Real Estate & Construction
- Retail
- Software & Internet
- Telecommunications
- Transportation & Logistics
Our 5-Step Process to Cloud Security
- Assessment and Planning: We first invest time to understand your current security requirements and the compliance standards to identify potential security threats in your cloud environment. Based on the assessment, we develop a foolproof security strategy for your cloud.
- Infrastructure Security: After a planned strategy, our team of experts helps implement security measures for data centers and establish a secure network to prevent network-based attacks.
- Identity and Access Management: A multi-factor authentication is set up to be able to control access across all cloud resources. Regularly auditing user access permissions is of utmost importance to avoid any threats.
- Threat Detection and Monitoring: We assist you in implementing a real-time monitoring system in case of any security mishappenings. While monitoring is ongoing, setting up security alerts helps with uncalled threats.
- Backup & Disaster Recovery: In the end, we provide you with a backup for all your cloud data and assist in building a disaster recovery solution to ensure data availability and integrity.
Benefits realized after taking up cloud security
- DDoS Protection: Incorporating cloud security ensures you have the most efficient protection against the rising occurrence, intensity, complexity, and gravity of DDoS attacks.
- Data Security: With a cloud security solution, your infrastructure is automatically designed to have the best data security, including security policies and protocols.
- Reduced Costs: No upfront investment on the services you consume; pay only for the resources you utilize, as cloud does not require any dedicated hardware.
- Advanced Threat Detection: Endpoint scanning, along with global threat intelligence, makes it relatively easier to detect threats in a cloud environment.
- Regulatory Compliance: Leading cloud security providers ensure regulatory compliance through enhanced infrastructure and managed services.
- Steep Rise in Customer Trust: When you have the best cloud security for your organization, that ensures that all your customer data is safe and secure. This gives your brand an upper hand while also gaining customer trust in the process.
Exiting Cloud
In rare cases, businesses may want to exit the cloud due to unavoidable circumstances. This scenario is rare since most companies quickly realize the benefits the cloud delivers within months of adoption. Rapyder can completely support your migration to a new environment from the cloud if an imminent drop from cloud is necessary.
24*7 customer support
We provide 24/7 dedicated customer support for all unexpected situations with minimal downtime without compromising customer convenience.
Our Partners

Our Customers

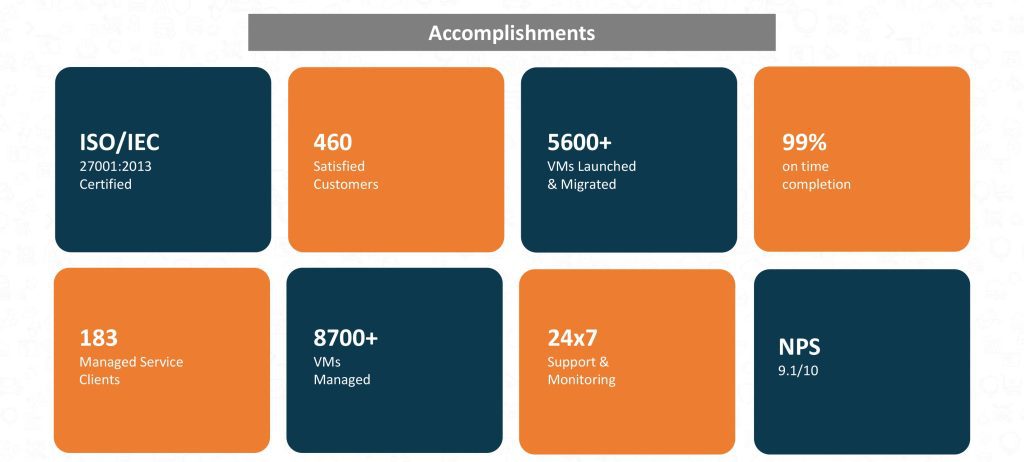
Our Accomplishments